Zoom security flaw meant random people could have spied on your calls
Bug could have been used to snoop on virtual cabinet meeting, researcher suggests

Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
Your support makes all the difference.A security flaw with Zoom meant hackers could enter password-protected calls "in a matter of minutes", a researcher has revealed.
The issue stemmed from a lack of limits on the number of times a password could be attempted on private meetings.
Video chats were protected by default by a 6 digit password, meaning there were 1 million possibilities. Attackers could therefore brute force all the different combinations relatively quickly and easily.
The vulnerability was discovered by Tom Anthony, vice president of Product at SEO firm SearchPilot, who first reported it to Zoom on 1 April.
Details of the exploit were only publicly disclosed on Wednesday, though Zoom said that the issue was mitigated on 9 April, meaning any calls after that date were no longer vulnerable.
There is no evidence that the security flaw was used by hackers, but the nature of such attacks mean it would be nearly impossible to find out.
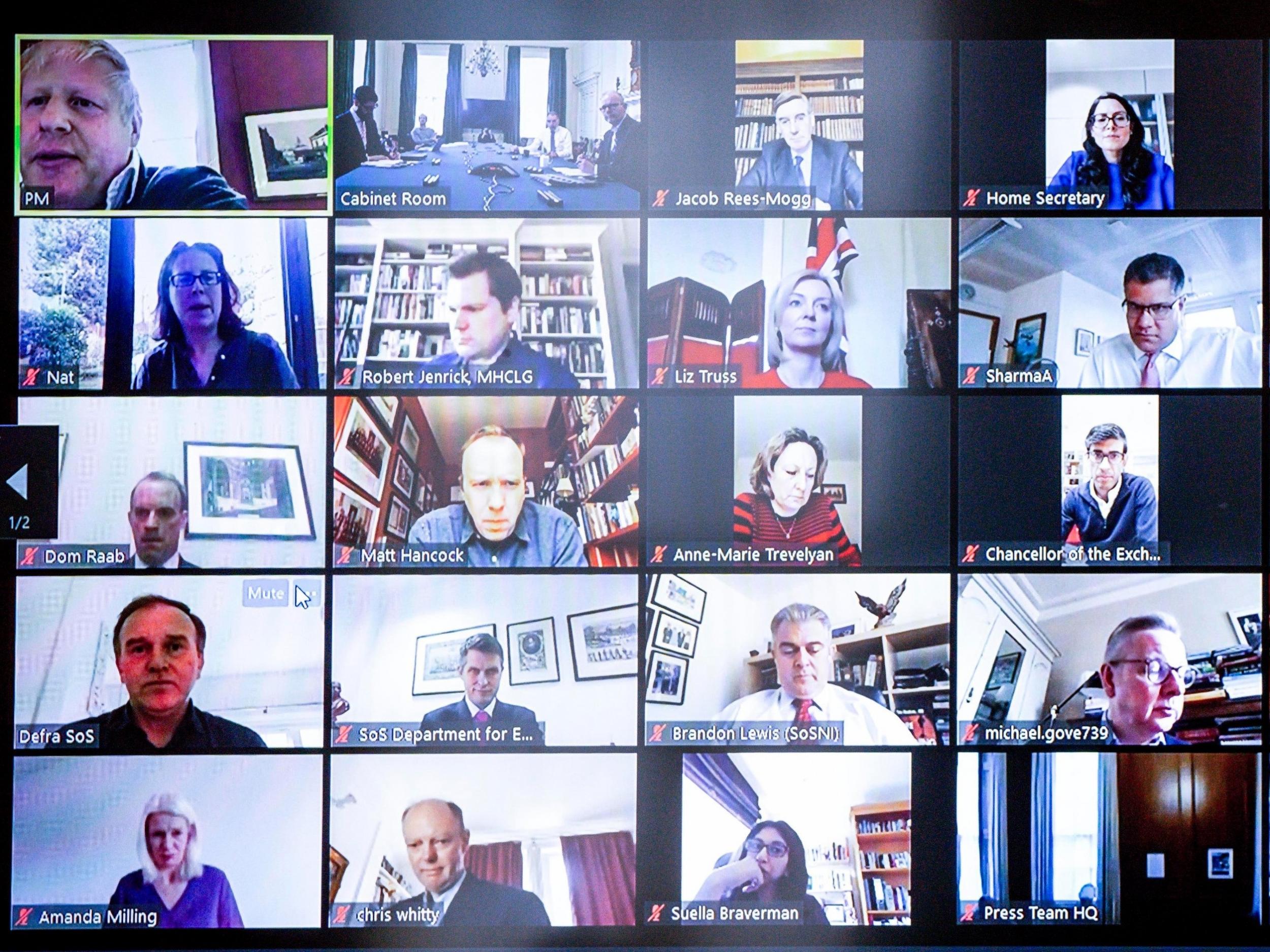
Mr Anthony suggests it could have been used in highly-confidential meetings that took place over the video chat platform during lockdown measures introduced in late March to contain the coronavirus pandemic.
"On 31 March, Boris Johnson tweeted about chairing the first ever digital cabinet meeting. I was amongst many who noticed that the screenshot included the Zoom Meeting ID," Mr Anthony wrote in a blog post detailing the bug.
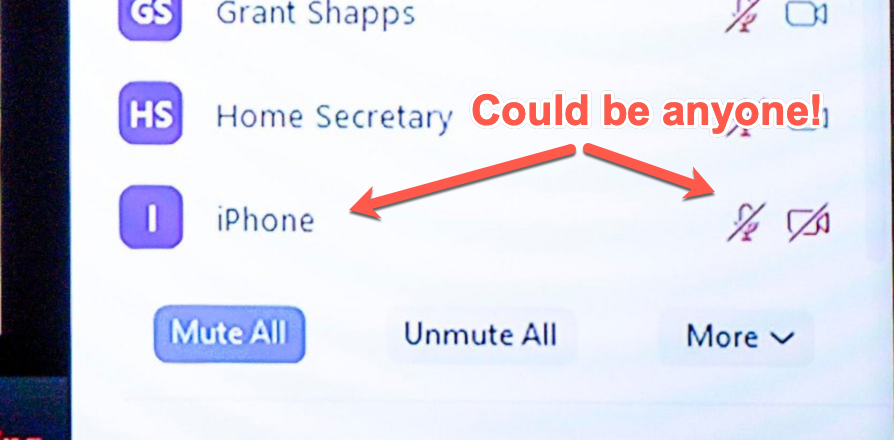
"I noted in Boris Johnson's screenshot that there is a user simply called 'iPhone' that is muted with the camera off. It got me wondering whether this flaw has previously been found - if I could discover it then it seems plausible that others could too, which makes this bug particularly worrisome."
It is the latest in a series of issues with the platform, which saw a trend known as 'Zoombombing' emerge in March and April, whereby people would enter video calls uninvited.
In the most severe instances, participants were subjected to footage of child sex abuse.
In response to the latest disclosure, a spokesperson for Zoom told The Independent: “Upon learning of this issue we immediately took down the Zoom web client to ensure our users’ security while we implemented mitigations.
"We have since improved rate limiting... and relaunched the web client on 9 April. With these fixes, the issue was fully resolved, and no user action was required. We are not aware of any instances of this exploit being used in the wild."
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments