Thunderspy attack: How to protect your Mac, Windows or Linux computer from hackers
If you want to ensure your computer is kept safe, this is everything it is vital to know

Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
Your support makes all the difference.The Thunderbolt port used on computers and laptops has been found to have a serious vulnerability, one that allows a hacker to access the contents of your device within minutes.
The port is a connection made by Intel and Apple that allows for faster data transfer through a physical cable.
While the hacker will need physical access to your computer, the level of control they would have should they get it is astounding; your device could be encrypted, password-protected, and locked, and yet could still be bypassed in under five minutes.
The attack, called “Thunderspy” affects personal computers running Microsoft’s Windows operating system, Apple Macs from 2011 with Thunderbolt connectivity (other computers running MacOS are affected partially), and devices using Linux.
Since this vulnerability could affect a number of mainstream computers, users should check their systems and ensure they’re protected. Here’s everything you need to know:
What is the Thunderbolt connection?
The Thunderbolt connection looks similar to the USB-C port on many laptops and smartphones.
However, Thunderbolt devices come with a lightning symbol on the connection and usually with a “3” near it if the device supports 40Gb/s throughput.

How could hackers access my system?
The example researchers give is called an “evil maid attack”. Speaking to Wired Björn Ruytenberg, the researcher that discovered Thunderspy, said that “all the evil maid needs to do is unscrew the backplate, attach a device momentarily, reprogram the firmware, reattach the backplate, and the evil maid gets full access to the laptop”.
How concerned should I be?
That depends. Although the attack requires a certain level of knowledge of, as well as physical access to, your computer, the speed at which the protections can be bypassed is surprising and worrying. As with most things, better to be safe than sorry.
How do I check if my Windows computer is affected?
The researchers that discovered this vulnerability recommend their own verification tool Spycheck or users can check their computer manually by comparing symbols on their computers.
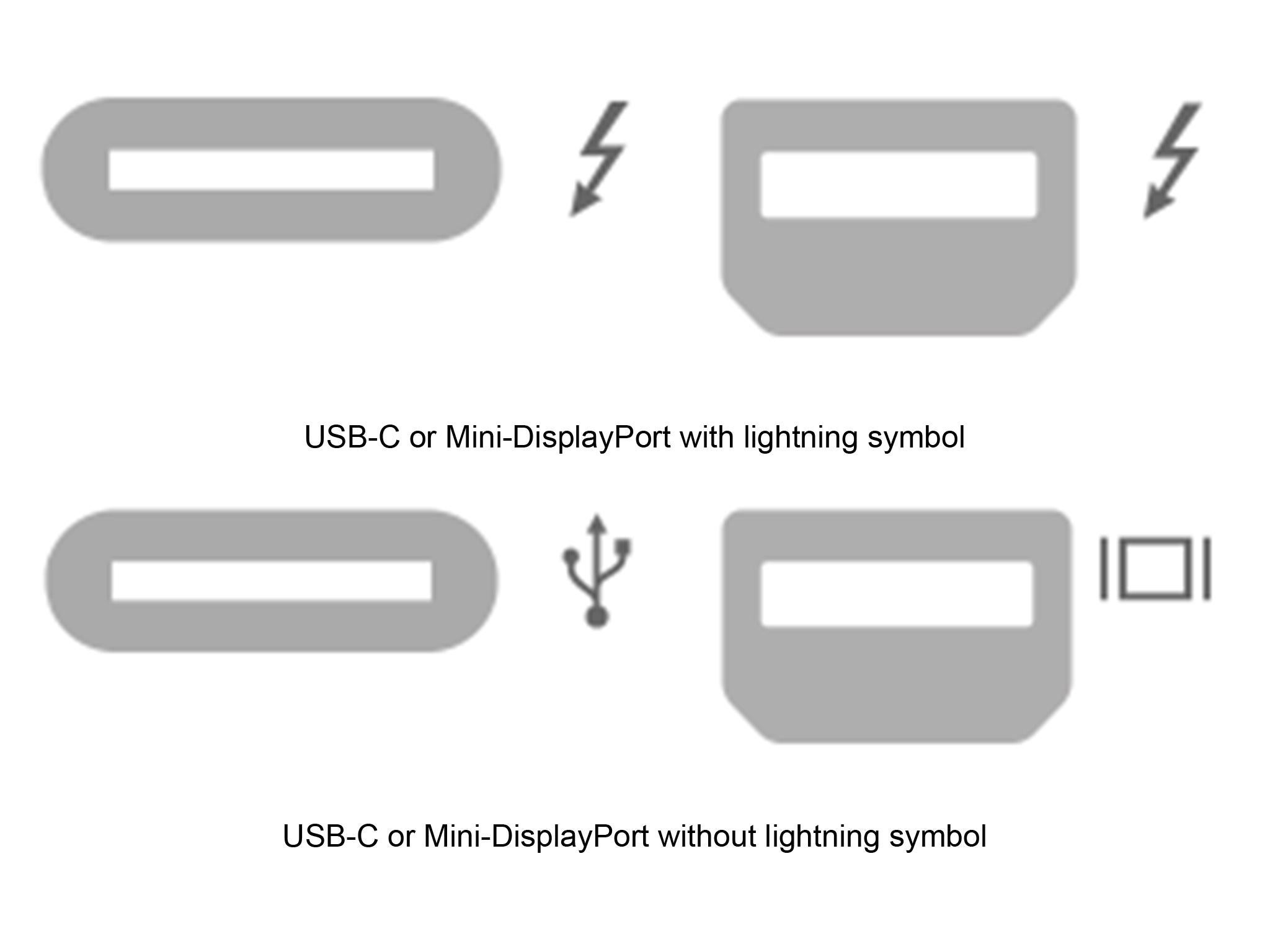
If your system has any of the port symbols on the top row, it has Thunderbolt connectivity and is therefore vulnerable.
Those that purchased their computers before 2019 do not have a fix available. Those purchased after 2019 should check whether their system supports Kernel DMA Protection – explained further down - to mitigate the vulnerability, however it is adequate to simply follow the steps later on to manage your Thunderbolt peripherals.
How do I check if my Apple computer is affected?
The Thunderspy vulnerability could affect all Apple Macs from 2011, apart from Retina MacBooks. This includes:
- iMac Pro
- iMac models from 2017
- Mac mini (2018)
- MacBook Pro models from 2016 or later
- MacBook Air (Retina, 13-inch, 2018)
But those computers are much more at risk if they are using another operating system, such as Windows or Linux, rather than Apple's own MacOS. While Apple computers running MacOS could still theoretically be hit, the operating system integrates many of the more recent security updates that keep users protected.
Apple said in a statement that some hardware securities features that protect against such attacks are only enabled when a computer is running MacOS, and that anyone concerned about the issue should ensure they are running its operating system.
How do I check if my Linux computer is affected?
Linux users are also recommended to follow the same steps as those with Windows computers, although the researchers’ Spycheck tool will require root privileges to generate an accurate report.
What should I do if I need to continue using my Thunderbolt connection?
There are a number of steps you can take to mitigate the risks. These are:
- Only connecting your own Thunderbolt peripherals to your computer, and do not lend them to others.
- Do not leave your system unattended when it is turned on.
- Do not leave your peripherals unattended.
- Avoid using sleep modes.
What should I do if I do not use my Thunderbolt connection?
It is possible to completely control the Thunderbolt controller in your computer’s BIOS. BIOS is firmware installed on your computer which is used to boot hardware when your computer starts up. However, you should only do this if you are confident in your knowledge of your computer’s operating system.
Is my USB-C connection affected?
USB-C connections are not affected.
What is Kernel DMA Protection?
Kernel DMA Protection protects Windows PCs against attacks some attacks via the Thunderbolt 3 port, however it is only available on select computers. The models supported, and the way to enable the protection, are as follows:
- HP EliteBook and ZBook (2019 and later): Power on the system and press F2. In the “Startup Menu” screen, select “BIOS setup (F10)”. From the “Advanced” menu, select “System Options”. In the screen that follows, verify “DMA Protection” is enabled.
- Lenovo ThinkPad P53, X1 Carbon (2019 and later): Power on the system and press F1. From the “Security” tab, select “Virtualization”. In the screen that follows, verify “Kernel DMA Protection” is enabled.
- Lenovo Yoga C940 (models with “Ice Lake” CPU only): Always enabled by default. Status cannot be queried from UEFI.
What has Intel said?
Intel published a blog post claiming that “underlying vulnerability is not new and was addressed in operating system releases last year [and that] the researchers demonstrated new potential physical attack vectors using a customized peripheral device on systems that did not have these mitigations enabled.”
The researchers disagree with this, arguing in Wired that the vulnerability is new, and that their attack uses commonly-found, ‘off-the-shelf’ components.
Intel has said that operating systems with Kernel Direct Memory Access (DMA) protection can mitigate these attacks, although as mentioned earlier, few systems have such protections.
“For all systems, we recommend following standard security practices, including the use of only trusted peripherals and preventing unauthorized physical access to computers” the company stated.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments