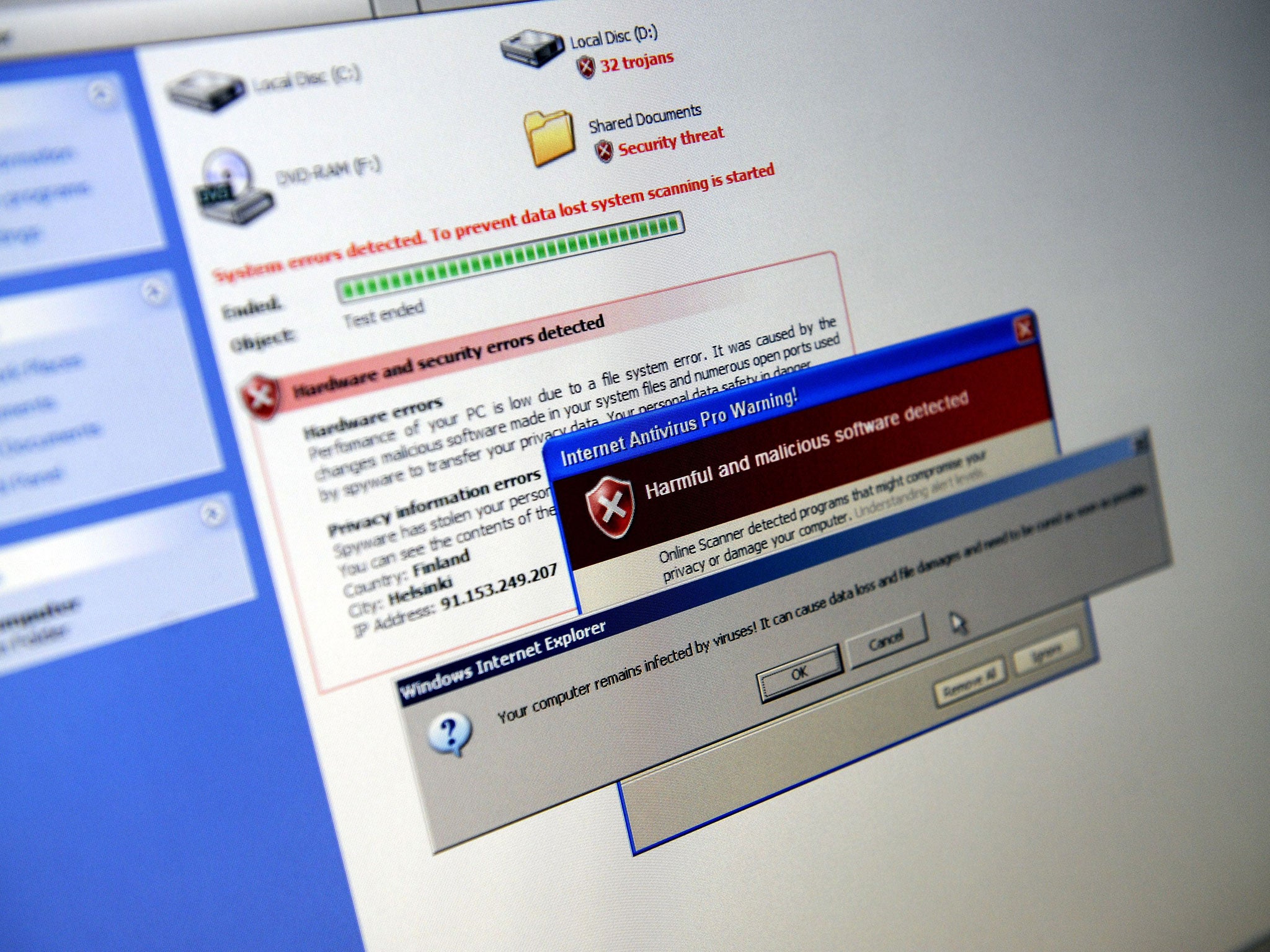
Regin: Newly uncovered malicious software snooping since 2008 'was developed by a nation state'
The malware uses several 'stealth' features and even when its presence is detected, it is very difficult to work out what it is doing
Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
Your support makes all the difference.An advanced malicious software application has been uncovered that since 2008 was used to spy on private companies, governments, research institutes and individuals in 10 countries, antivirus software maker Symantec Corp said in a report on Sunday.
The Mountain View, California-based maker of Norton antivirus products said its research showed that a "nation state" was likely the developer of the malware called Regin, or Backdoor.Regin, but Symantec did not identify any countries or victims.
Symantec said Regin's design "makes it highly suited for persistent, long-term surveillance operations against targets," and was withdrawn in 2011 but resurfaced from 2013 onward.
The malware uses several "stealth" features "and even when its presence is detected, it is very difficult to ascertain what it is doing," according to Symantec. It said "many components of Regin remain undiscovered and additional functionality and versions may exist."
Almost half of all infections occurred at addresses of Internet service providers, the report said. It said the targets were customers of the companies rather than the companies themselves. About 28 percent of targets were in telecoms while other victims were in the energy, airline, hospitality and research sectors, Symantec said.
Symantec described the malware as having five stages, each "hidden and encrypted, with the exception of the first stage." It said "each individual stage provides little information on the complete package. Only by acquiring all five stages is it possible to analyze and understand the threat."
Regin also uses what is called a modular approach that allows it to load custom features tailored to targets, the same method applied in other malware, such as Flamer and Weevil (The Mask), the antivirus company said. Some of its features were also similar to Duqu malware, uncovered in September 2011 and related to a computer worm called Stuxnet, discovered the previous year.
Cybersecurity is a sensitive topic for businesses in the United States, where there have been several breaches of major companies and customer information. The US government and private cyber intelligence firms have said they suspect state-backed hackers in China or Russia may be responsible.
Symantec said Russia and Saudi Arabia accounted for about half of the confirmed infections of the Regin malware and the other countries were Mexico, Ireland, India, Iran, Afghanistan, Belgium, Austria and Pakistan.
REUTERS
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments