NHS cyber attack: New dangerous version of WannaCry ransomware set to be released by hackers
‘Version 1 of WannaCrypt was stoppable but version 2.0 will likely remove the flaw. You're only safe if you patch ASAP,' says accidental hero, 22, who shut down major attack
Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
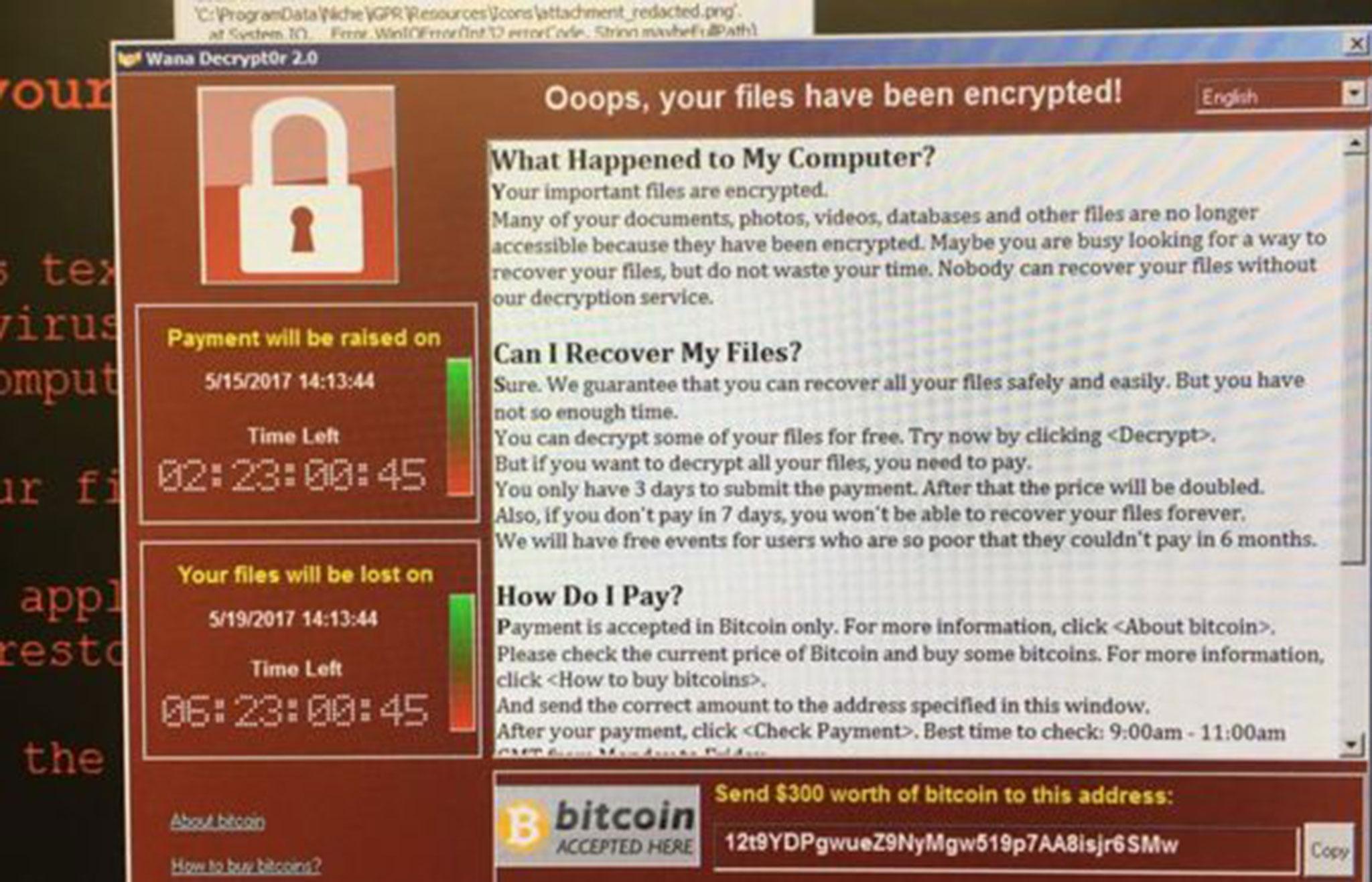
Your support makes all the difference.A second version of the devastating WannaCry ransomware – that does not contain the “kill switch” used by a 22-year-old security analyst to shut down many attacks – is set to be released by the hackers, putting more computers at risk.
Costin Raiu, of web security firm Kaspersky Lab, told Hacker News that they had already seen versions of the malware that did not contain the website domain name used to shut down the program, but he later backtracked saying “my bad” and this was not actually the case.
However, experts warned it was likely only a matter of time before this did happen and urged people to instal a security patch released specially by Microsoft.
Hidden in the code was an unregistered web address, which the virus would always try to contact when first infecting a computer. If it received a reply, it would shut down, but if not it would carry out the attack.
A 22-year-old security analyst known as MalwareTech, who wishes to remain anonymous, registered the website, unknowingly activating the shutdown process.
However, he warned that it would be easy for the hackers to change the coding in a “worm” used to infect computers with WannaCry to remove the domain name.
MalwareTech also told Hacker News that they had only stopped one version of WannaCry, which is known by various versions of the name.
“WannaCrypt ransomware was spread normally long before this and will be long after, what we stopped was the SMB worm variant,” he said, referring to the program that affected nearly a fifth of NHS Trusts in England and scores of businesses and government departments around the world.
And in a message on Twitter, he wrote: “Version 1 of WannaCrypt was stoppable but version 2.0 will likely remove the flaw. You’re only safe if you patch ASAP.”
He also retweeted a message saying people who were unable to patch their computer could disable Server Message Block version 1 (SMBv1), linking to Microsoft’s instructions about how to do this.
Mr Raiu wrote on Twitter that his initial belief that the kill switch had been removed from WannaCry had been mistaken.
“My bad – finished analysing all #Wannacry worm mods we have and they all have the kill switch inside. No version without a kill-switch yet,” he said.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments