Adult live-streaming site CAM4 exposes millions of models' personal information
First and last names, email addresses, gender and sexual orientation, and credit card information of models and users was left on an insecure server

Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
Your support makes all the difference.An unprotected database for the adult live-streaming website CAM4 has left millions of people’s personal information available to the public and could be used by criminals to commit fraud.
Information left insecure on the website's database includes first and last names, email addresses, gender and sexual orientation, device information, payment logs including credit card types, transcripts of emails, IP addresses and password hashes, researchers said.
Password hashes are converted passwords – written as strings of incomprehensible characters – that are supposed to be converted back to readable text.
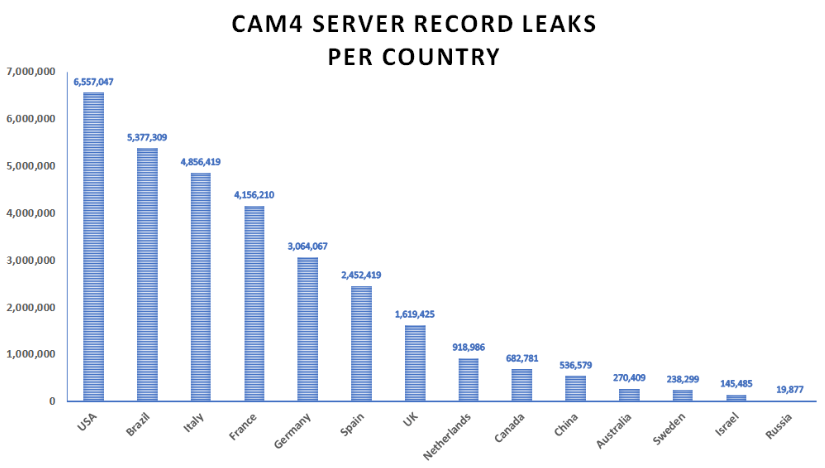
According to a team of researchers from Security Detective a 7TB database contained over 10.88 billion records dating back to 16 March.
US, Brazilian and Italian users were the worst affected, although the exact scale of the vulnerability is difficult to know as multiple entries were duplicated.
Most concerning were the few hundred cases where full names, credit card types, and payment information were grouped together, as that information used together could be used by to get access to even more sensitive information.
Many of the emails were from major domain names such as Gmail, iCloud, and Hotmail.
It is unclear how the information left vulnerable relates between models and content viewers, as everyone with a CAM4 account can broadcast if they choose to, and the researchers were not able to differentiate between performers and viewers.
The breach also had information related to fraud and spam detection, which means that hackers could have had greater insight into the live-streaming site’s security defences.
The researchers said that the logs enable hackers to see how security systems have been set up and “could be used as an ideal verification tool for malicious hackers, as well as, enabling a greater level of server penetration. Moreover, website backend data could be harnessed to exploit the website and create threats including ransomware attacks.”
“Possibly the greatest risk in both financial and reputational respects is the risk of blackmail scams that could be deployed against users who believe they are anonymous when sharing compromising data and content,” the researchers continued.
This is not the only instance where an adult site has left its users’ personal information insecure. Affair website Ashley Madison infamously had 37 million personal records accessed by hackers who threatened to reveal the data if the site was not shut down.
Other services, including the Marriott hotel chain, British Airways, and Uber have also exposed users’ private data in the past.
UPDATE 13.05.20: Following publication of this article CAM4 has asked us to make clear that there was no malicious security breach resulting in the loss of personal data from any CAM4 server worldwide. The company says that developers and security specialists were deployed immediately for further investigation, and the team concluded without any doubt that absolutely no personally identifiable information, including names, addresses, emails, IP addresses or financial data, was improperly accessed by anyone outside the SafetyDetectives firm and CAM4’s company investigators.
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments