3fun: Security glitch in threesome hook-up app reveals details of users in Downing Street and White House
‘Worst security of any dating app we’ve ever seen,’ say experts

Your support helps us to tell the story
From reproductive rights to climate change to Big Tech, The Independent is on the ground when the story is developing. Whether it's investigating the financials of Elon Musk's pro-Trump PAC or producing our latest documentary, 'The A Word', which shines a light on the American women fighting for reproductive rights, we know how important it is to parse out the facts from the messaging.
At such a critical moment in US history, we need reporters on the ground. Your donation allows us to keep sending journalists to speak to both sides of the story.
The Independent is trusted by Americans across the entire political spectrum. And unlike many other quality news outlets, we choose not to lock Americans out of our reporting and analysis with paywalls. We believe quality journalism should be available to everyone, paid for by those who can afford it.
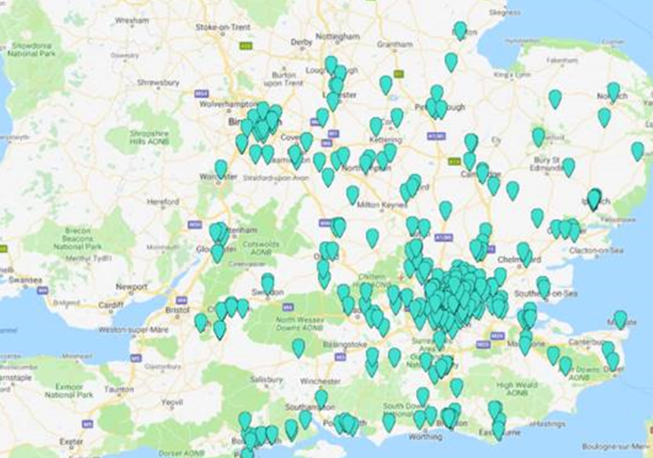
Your support makes all the difference.A dating app designed for arranging threesomes has been described as a “privacy train wreck” by security experts after the software was found to reveal real-time locations, birth dates, chat data and even photographs of its 1.5 million users.
The app, 3fun, revealed users with locations appearing to be in No 10 in London, and the White House and the US Supreme Court in Washington DC, according to a report on cyber security firm Pen Test Partners’ website.
Other dating apps, including Grindr, Romeo and Recon have recently also been found to have been revealing the exact location of users, but in those cases users’ precise locations were calculated by triangulating distances from three different places. On 3fun, the exact co-ordinates, accurate to within a building, were accessible through the app.
Furthermore, private photographs were accessible too.
Pen Test Partners said 3fun had “probably the worst security for any dating app we’ve ever seen”.
Users of the app could restrict the app from showing their locations, but according to Pen Test Partners, the data was only filtered on the mobile app itself, not on the servers containing the data, which their experts were able to query to reveal location information.
While the data the security company saw revealed users with locations in No 10, the White House, and the US Supreme Court, Pen Test Partners’ Alex Lomas said: “It’s technically possible to re-write one’s position, so it could be a tech savvy user having fun making their position appear as if they are in the seat of power.”
He added: “There are definitely some ‘special relationships’ going on in seats of power.”
In their analysis, Pen Test Partners also used the vulnerable data to calculate the number of users listing themselves as straight men, compared to the number of users whose profiles state they are straight women, and found a ratio of four straight men to every one straight woman.
Sexual preference and relationship status could also be queried.
Pen Test Partners contacted 3fun on 1 July pointing out the data had been compromised and advised them to fix the security flaws.
In a text message, 3fun reportedly replied: “Dear Alex, Thanks for your kindly reminding. We will fix the problems as soon as possible. Do you have any suggestion? Regards, The 3Fun Team”.
While Pen Test Partners said the text was “a little concerning”, they noted the company took action quickly and resolved the problem.
A spokesperson for 3Fun told tech news website The Verge the company had updated the app on 8 July and added: “We will focus on updating our product to make it safer.”
Join our commenting forum
Join thought-provoking conversations, follow other Independent readers and see their replies
Comments