The Zero Trust model addresses vulnerabilities in converged manufacturing environments
THE ARTICLES ON THESE PAGES ARE PRODUCED BY BUSINESS REPORTER, WHICH TAKES SOLE RESPONSIBILITY FOR THE CONTENTS

Palo Alto is a Business Reporter client.
As OT converges with IT, manufacturers must overcome skills gaps and new cyber-threats – and Zero Trust is here to help
Operational technology (OT) systems are experiencing an increasing number of cyber-attacks. In the2023 Unit 42 Extortion and Ransomware Report, Palo Alto Networks Unit 42 found that last year, manufacturing was one of the most affected sectors in terms of extortion attacks
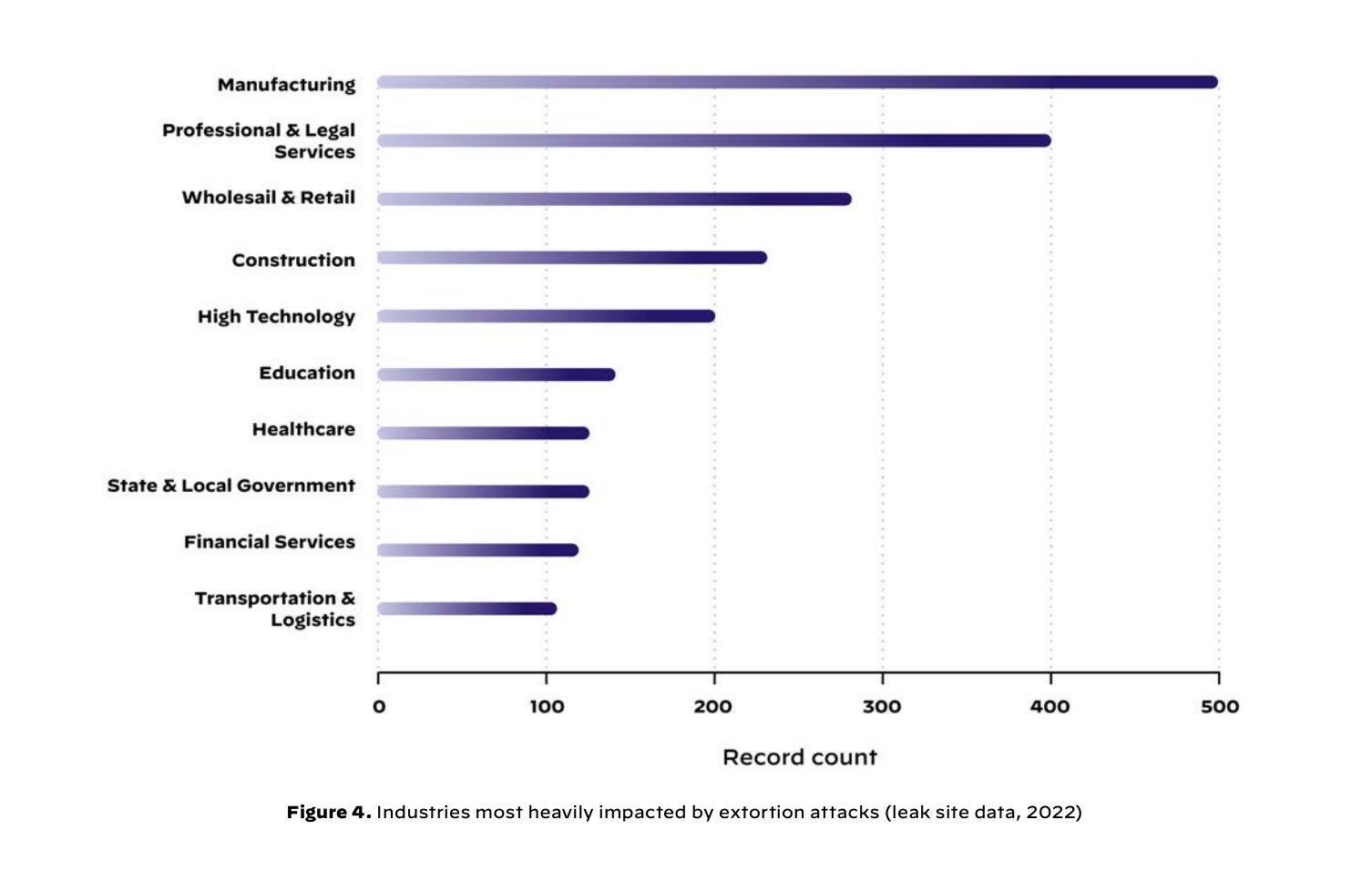
OT system attacks can yield significant consequences, such as leakages, outages, shutdowns or even physical harm to humans. Late last year, Simpson Manufacturing, an engineering and manufacturing company, shut down systems upon detecting malicious activity from its IT infrastructure. Although the full impact of the shutdown was uncertain, the company reported in its 8K-Form filing to the United States Securities and Exchange Commission that the attack had caused ongoing disruption to its manufacturing operations, and ultimately engaged a third party to investigate and aid in recovery efforts.
Manufacturing is a prime target for several reasons. Fortunately, a Zero Trust approach can help companies regain control and design a stronger security strategy.
Modern challenges facing the industry
IT and OT systems have increasingly converged as digital transformation has become widespread. Consequently, once-isolated OT systems are now internet-connected. This makes them accessible to attackers and increases cyber-risk.
The infrastructure of the manufacturing industry is often dependent on legacy systems, which also heightens the security risk. Many of these systems run unsupported and outdated operating systems that didn’t take cyber-security into account. Those systems are hard to upgrade or patch because of warranty, compliance and operational challenges.
There’s also a skills shortage when it comes to managing converged IT/OT environments. In aNational Association of Manufacturers survey, three quarters of participants noted that a major business challenge was attracting and keeping a skilled workforce. ISC2’s current estimate of the worldwide cyber-security skills gap runs to four million people. And locating professions who have both OT and security skills is even harder.
More ransomware, more regulations
Manufacturers are trying to address these challenges while also feeling the pressure to maintain operations uptime. A ransomware attack against a factory can hamstring production: it can take days or weeks to get up and running again, which impacts the bottom line. Cyber-criminals are taking advantage of this vulnerable state. OfUnit 42’s client base, manufacturers are the second most-targeted sector.
Governments have taken notice of increased risk and have added more regulations. For instance, the US Securities and Exchange Commission now mandates a cyber-incident reporting window of just four days for larger, publicly traded companies. That includes manufacturers, and it adds to the cybersecurity pressure on them to act fast.
Grappling with increased complexity and convergence
Manufacturers have a variety of environments to defend. They must manage OT networks – such as the factory floor – and devices, remote operations and next-generation 5G-connected networks and devices. No one – not OT or IT managers – has a comprehensive view of all these varying devices, systems applications and environments.
This adds to the challenge of operating highly complex systems and creates massive cyber-risk. For all the reasons noted so far, tech teams often can’t keep pace with these threats and stop them.
A Zero Trust approach can resolve many of these challenges, particularly at a factory’s higher architectural layers, where IT/OT convergence first occurs. Zero Trust assumes no person or device is trustworthy until verified at each step of a digital interaction. Zero Trust provides the same security for infrastructure, applications, devices and users throughout the company. This approach makes securing the variety of environments within a factory easier.
To deploy a Zero Trust approach, organisations need to aim for three things:
· Comprehensive visibility – This includes identifying every device and getting an understanding of behavioural and transactional flow. To assess risk and know which Zero Trust policies to create, broad visibility is an essential component.
· Zero Trust for every environment – Organisations need to ensure all environments are covered, with least-privilege access policies, built-in policy enforcement, continuous trust verification and continuous security inspection.
· Ease of operation – Today many companies have built out multiple point solutions to cover different OT environments and challenges. This creates gaps in data flow and fragments the user experience, leading to security challenges and increased cost. A comprehensive Zero Trust approach provides a broad solution that’s easy to operate, to eliminate gaps and reduce cost.
Securing converged environments
OT environments will continue to face an increase in cyber-threats and attacks. Couple this with a skills shortage and legacy systems, and it’s a recipe for significant risk to business operations and human safety. As the IT/OT convergence continues, manufacturers are adopting Zero Trust principles to maintain operational resilience, reduce new or increased risk caused by digital transformation, and shrink the attack surface. These newer converged environments pose many challenges, but adopting a Zero Trust approach lays the foundation for a more robust security profile in the complex manufacturing landscape.
Palo Alto Networks has a leading solution to address these challenges. For more information on how to implement Zero Trust OT security for zero downtime, click here.

Bookmark popover
Removed from bookmarks